In industrial applications, performing monitoring, maintenance, and diagnostics remotely can help push the boundaries of industrial manufacturing and significantly reduce operational costs. However, when performing monitoring and control on Ethernet networks, data packets are susceptible to being intercepted by malicious attackers. For example, if hackers gain access to the network, they can use any packets that they intercept to interpret the network topology, which will give them complete control over the system. Therefore, preventing access to data transmission across industrial networks is vital. In order to combat this risk, network operators should consider the following features when deploying remote access for their industrial applications:
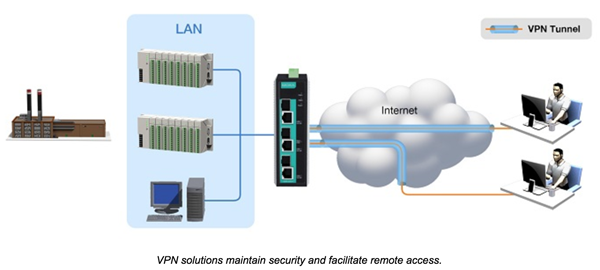
1. IPsec VPN Servers to Facilitate Secure Remote Access
Network operators based in the control room frequently use the Internet to gain access to remote sites. The operator should utilize a gateway that not only functions as a firewall and authenticator to the network, but also supports IPsec VPN functionality. VPNs create a virtual encrypted tunnel that connects remote locations with control centers to ensure confidentiality when IP packets are transmitted. IPsec also supports secure authentication and data integrity, which are the two key requirements when transferring packets on industrial networks. Therefore, using IPsec VPN servers ensures control and monitoring data is protected through use of strong encryption methods.
2. LAN Security, Port Access, and the 802.1x Protocol
Protocols such as RADIUS and TACACS+ support authentication mechanisms that make it difficult for hackers who use the Internet to gain direct access to the network or devices. RADIUS encrypts the transmission of the user password and TACACS+ encrypts all the key authentication parameters. In addition, devices on the network should support additional authentication measures to prevent a user from simply connecting a laptop directly to an open Ethernet port on a piece of network equipment. One option available to network operators is to utilize the 802.1x protocol, which uses a port-based authentication method to authenticate devices that try to gain access to the protected network. The devices must provide authentication credentials such as a username and password or a security certificate before gaining access to the network.
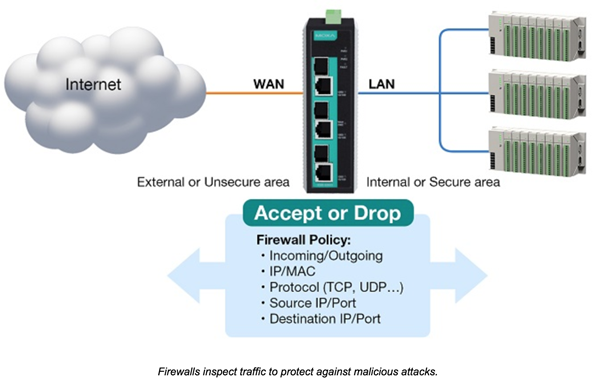
3. Deploying a Firewall Between PLCs/RTUs and External Traffic
A stateful inspection firewall monitors all incoming and outgoing packets. The firewall will either block packets or allow them to pass depending on its preconfigured rules. In addition, the firewall needs to be able to guard against malicious attacks without diminishing the performance of the network. In order to achieve this, network operators need to deploy devices with embedded software that sit at the edge of the network, and they must be capable of protecting the network with minimal latency. It is also advisable to use a firewall that has industrial fieldbus settings, which allows automation engineers to easily implement necessary restrictions without having to perform any complex procedures.
4. DMZs for Public or Shared Servers
A demilitarized zone (DMZ) is often employed in IT solutions, but can also serve as a strong defense mechanism in automation networks. In order to perform remote monitoring or maintenance, some of the data servers or HTTP servers will need to be accessed from public networks or the Internet by different operators. In order to maintain high levels of security on industrial networks, any shared servers should be isolated into different networks by utilizing DMZs. Deploying a network topology that uses DMZs allows general operators to only access the shared servers and not the control network. The main benefit of restricting user access is that if a user with malicious intent gains access to the network, they will not have access to the entire network, which limits the damage they can cause.
5. Industrial-Grade Devices
A security device deployed in industrial applications needs to be hardened as unmanned remote sites do not often provide environmental control beyond a secure enclosure. Therefore, the device needs to be able to operate reliably in a wide range of temperatures. If a non-industrial grade device that was not designed for harsh industrial environments is deployed, there is a high chance that it will fail. In addition to a durable and strong casing, the device should also support dual power inputs to provide backup power in the event that the primary power source fails.
Deploying a device with an IPsec VPN server allows engineers who need access to devices at remote sites to securely tunnel from the control center to multiple remote locations. However, only deploying VPNs does not suffice to mitigate risks. It is suggested to have multiple layers of protection such as LAN security, authentication, firewalls that inspect packets, as well as a DMZ that can isolate external and internal networks to further enhance network security. Without an industrial-grade secure gateway installed, access from remote locations over the Internet can be easily hacked using simple methods. Download the white paper to learn more about secure remote access for industrial applications.